In the federal government, cantons and municipalities too, the transformation into a “Digital Administration Switzerland” with a user-friendly and effective range of services for Swiss citizens is fully underway.
This brings with it greater connectedness and increasingly complex technologies, which in turn raise the risk of IT security and data protection issues. Again and again, reports about data theft, hacking attempts, and security gaps in digital applications cause commotion and uncertainty.
Security, compliance, data protection, and usability
To ensure that these newly created digital services are broadly accepted by the public, you need trust — without trust, any digitalization plan is doomed to fail. You build this trust by consistently adhering to the classic pillars of information security: confidentiality, integrity, and availability. In turn, these are achieved by adopting appropriate measures in technical security, compliance, data protection, and user-friendliness. Particularly in use cases which involve critical infrastructures or highly sensitive data — tax returns, issuing passports, digital signatures, for instance — these measures must be implemented consistently. Often, said measures are only “grafted” onto the purely functional solution after development, as a necessary evil, so to speak. This produces a kind of patchwork, with seams at which confidentiality, integrity, and availability can become easy prey to attackers.
Security at all phases of software development
The development of digital solutions requires a change in thinking. Security, protection, and compliance with regulatory systems need to be treated as an integral part of the solution, and thus addressed properly at all stages of the software development. This starts with the initial architectural sketches, continues with the cycle of unit tests, functional tests, and acceptance tests, and it doesn’t stop with deployment either. This “security by design” also guarantees that security, protection, and usability aspects are properly embedded, thanks to frequent updates and by swiftly enhancing the solution. In turn, this significantly boosts resilience against cyber attacks, ultimately increasing citizens’ trust in the digital service offered.
Agile development and security by design – a match made in heaven
This approach corresponds beautifully with one of the basic principles of agile development, namely that of built-in quality. At ti&m, therefore, we have seamlessly integrated the formulation of security requirements as well as security tests and checks into the agile work methods and ceremonies of our SAFe and Scrum processes. Security is an acceptance criterion for every story; special stories on security features and tests are obligatory in every iteration. In pair programming too, the app developer works alongside the security expert to ensure compliance with best practices for creating secure codes. Plus, security analysis tools are employed as part of the CI/CD process right from the outset. This has the effect of closely interweaving security measures with the development process without diminishing responsiveness or the speed of the agile process. Growing demand for cyber security in our products are thus represented transparently and precisely throughout the entire development cycle, and in a way that can be verified. All parties, from the client to the system engineer, gain awareness about security-related aspects and learn to view them as inherent measures that are not subject to negotiation. As accompanying measures, our engineers are actively trained and coached on this approach at our Academy.
Solid industry expertise, excellent technological know-how, and an understanding of the user and their requirements thus lead to safe and successful digital products at ti&m.
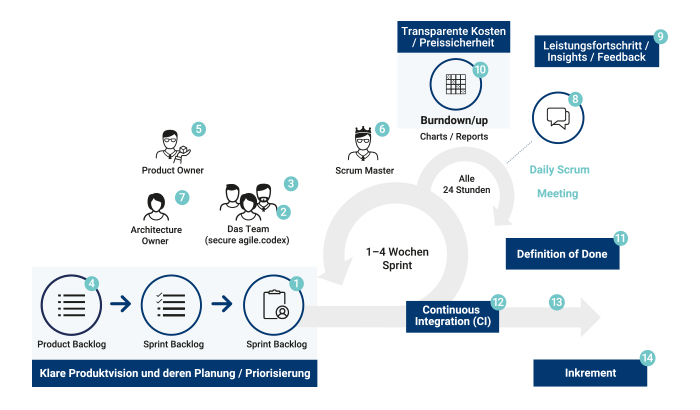
Secure Scrum
The following security measures are
covered in a sprint:
- Security refinement: Review and planning of security activities (threat assessment, risk management)
- Peer programming, preparation of features together with security experts
- Ongoing security testing
- Documentation of product hardening and security measures
- Refinement of stories by security experts
- Permanent contact partner for stakeholders (in contact with CISOs)
- Logging of existing security-related problems/impediments, training team members on security, organizing workshops, lectures, etc. if required
- Daily Scrum meeting for efficient communication
- Raising progress performance
- Keeping of burn down charts and reports
- Check definition of done requirements – glossaries, checklists, guidelines, and (code and business) guidelines
- Automated security checks by CI server
- Manual acceptance by security assessors in review meeting
- Storage of artifacts by CI server as releasable increment (including code, test, and documentation) & checking security risks for every release.
ti&m special e-government
What about the digital transformation of the public service? In our magazine ti&m special, we asked further digitalization experts from politics and government. to download