Improving the resilience of IT services with SBOMs
Software Bill of Materials // A SBOM is a list of all the software components, dependencies and metadata that are linked to an application. Automating the creation and maintenance of a precise list of software “ingredients” helps protect applications better.
To help an organization better understand the impacts of software vulnerabilities, an exercise can be carried out with a Red Team competing against a Blue Team. Unlike penetration testing, in this approach the attacking Red Team attempts to exploit gaps, while the Blue Team defends against the attack with countermeasures and security services. The major challenge here is that one exploitable vulnerability is enough for the Red Team to succeed, but the Blue Team has to protect all vulnerabilities.
As part of a study, an AI research team investigated the impacts of several large language models (LLMs) and open source vulnerability scanners as attackers in sandbox environments. The outcome — GPT-4 was able to exploit 87 percent of the vulnerabilities, while the other LLMs and the vulnerability scanners exploited 0 percent. If the vulnerability was not mentioned in a CVE Description (Common Vulnerabilities and Exposures), the level fell from 87 to 7 percent. The study shows how important it is to support the Blue Team in defending against such attacks. One option is to identify and eliminate vulnerabilities as quickly as possible using SBOMs.
NIST defines the minimum standards for SBOMs for the first time
At a three-day workshop attended by 1,400 people, the US National Institute of Standards and Technology (NIST) made the use of SBOMs mandatory. The intention is to achieve the following objectives:
All parties involved in the software supply chain develop a common understanding of the challenges posed by software weaknesses in terms of semantic interoperability.
Automating tools and processes can make it easier and faster to identify software with weaknesses.
With a higher degree of automation, the frequency of scans can be increased and/or adapted to the risk. Software that is available directly from the internet is checked more frequently than software that a team uses on the intranet.
Vulnerability management checks software with vulnerabilities for exploitability and replaces it with corrected versions or protects it using other measures.
And in Switzerland?
The Federal Office for National Economic Supply recommends measures to improve ICT (information and communication technology) resilience in the ICT Minimum Standard 2023 and offers an assessment tool for businesses and organizations to measure their own resilience. The decision to introduce SBOM-based processes brings improvements in the following areas:
Identify (ID)
Detect (DE)
Respond (RS)
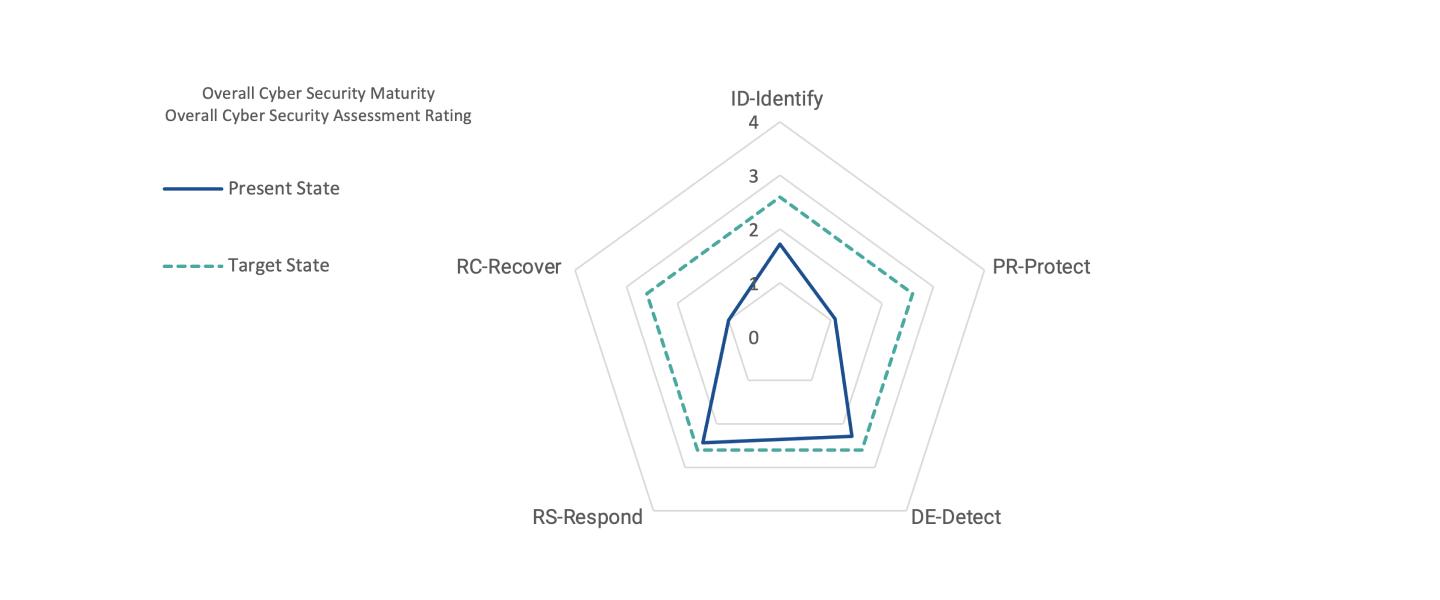
The diagram illustrates the outcome of such an assessment. We have expanded the assessment tool to make the effects of introducing an SBOM clearly visible —
without an SBOM, the maturity is 1 (partial), but with an SBOM it is 3 (repeatable). An organization that has automated its SBOM processing maturity is close to the
recommended ICT Minimum Standard for the Detect and Respond functions. It also improves the Identify function, while Protect and Recover must be addressed with other measures.
A tool like SBOM can significantly strengthen an organization’s ICT resilience. SBOM standardization and implementation in the tools along the software supply chain supports the Blue Team in eliminating vulnerabilities. Existing tools can automatically process standardized SBOMs from all suppliers, reducing manual tasks and
giving the Blue Team time to increase the maturity of
other processes that improve resilience.